Tchap: The super (not) secure app of the French government

On Wednesday 17th April 2019, the French Government launched a messaging application called “Tchap”. The day of the launch a lot of articles appeared:
-
“Tchap : The government launch a messaging app more secure than Telegram” Tchap : l'Etat lance une application de messagerie plus sécurisée que Telegram - PhonAndroid.com
-
“With Tchap, the government want to replace Telegram and WhatsApp” Avec Tchap, le gouvernement veut remplacer Telegram et Whatsapp
When I saw these titles, I remembered my work on Kimbho, an Indian app which was suppose to be the new WhatsApp. Spoiler: It didn’t end well for Kimbho: Patanjali’s messaging app is already a disaster
It’s 9am, I decided to analyse the app, you know… just to see if I can find something. My goal was to spend only 1 hour on it. I downloaded the app from the PlayStore, the current version was 1.0.22_a. As always, I started to use the app as a normal user to see the available functionalities. Argh, in order to create an account, you need to have a @gouv.fr or @elysee.fr email address. I have my first goal: create an account without having an @gouv.fr or @elysee.fr email address.
I decompiled the app and did the usual static analysis. Rapidly, I found out that the app is open source: dinsic-pim/tchap-android
This app is a fork of the Riot Android app. riot.im is a messaging app made by Matrix. They love open source, me too: Features | Riot
It’s time for the dynamic analysis. They implemented certificate pinning in the app. Of course, you can disable it with Frida ;) During the registration process, the app request a token
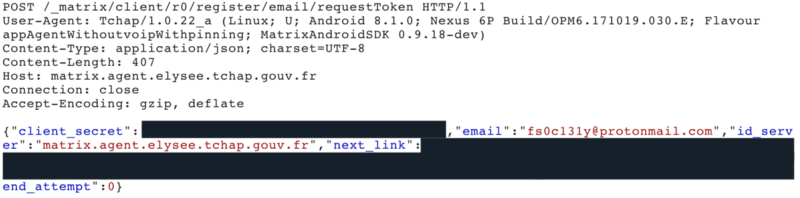
Depending of your email address, it will use the “correct” id_server. All the available servers are defined in the AndroidManifest.xml:
- matrix.agent.dev-durable.tchap.gouv.fr
- matrix.agent.dinum.tchap.gouv.fr
- matrix.agent.intradef.tchap.gouv.fr
- matrix.agent.diplomatie.tchap.gouv.fr
- matrix.agent.justice.tchap.gouv.fr
- matrix.agent.agriculture.tchap.gouv.fr
- matrix.agent.interieur.tchap.gouv.fr
- matrix.agent.social.tchap.gouv.fr
- matrix.agent.education.tchap.gouv.fr
- matrix.agent.finances.tchap.gouv.fr
- matrix.agent.ssi.tchap.gouv.fr
- matrix.agent.pm.tchap.gouv.fr
- matrix.agent.elysee.tchap.gouv.fr
- matrix.agent.culture.tchap.gouv.fr
- matrix.agent.tchap.gouv.fr
I set id_server to matrix.agent.elysee.tchap.gouv.fr. For info, Elysée is the French presidential palace. As I choose this server I guessed I should have an @elysee.fr email address. So, in the requestToken request, I modified email to fs0c131y@protonmail.com@elysee. Hum, no validation email in my inbox…
Wait, maybe it is waiting a known @elysee.fr email address. So I did a Google search “email @elysee.fr”
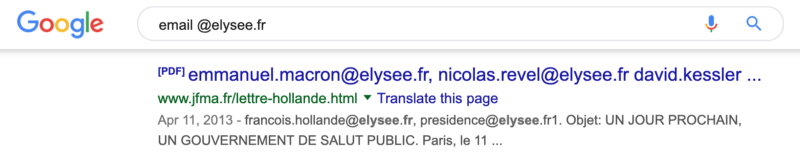
So I did another try and in the requestToken request and I modified email to fs0c131y@protonmail.com@presidence@elysee.fr. Bingo! I received an email from Tchap, I was able to validate my account!
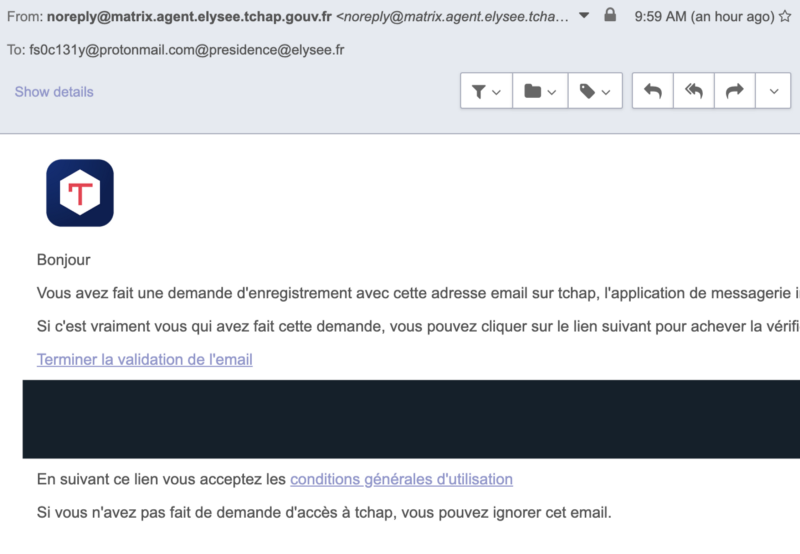
hacker voice: I’m in.
I am logged as an Elysée employee and I had access to the public rooms.
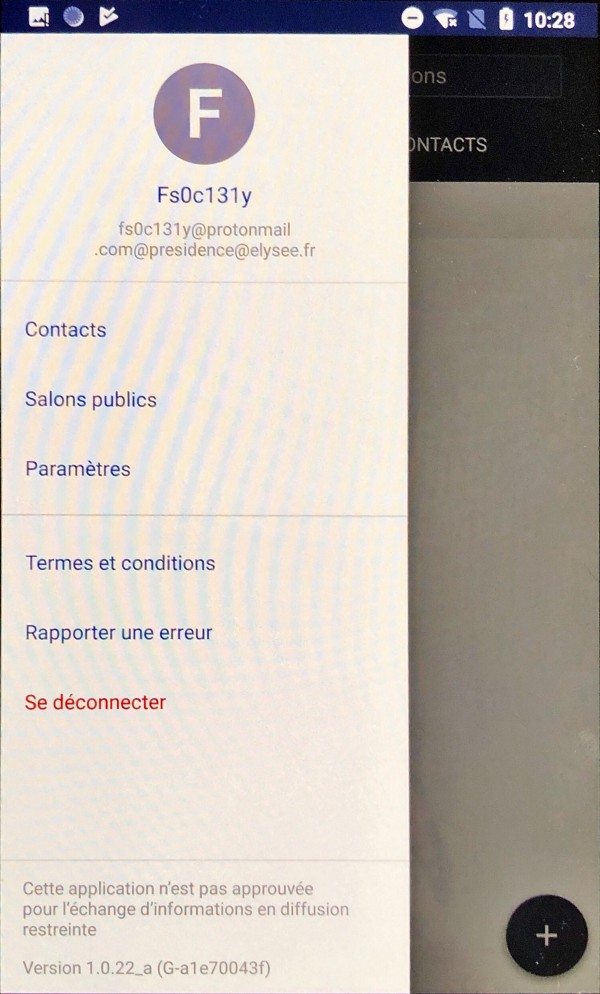

Funny thing: an employee of the Ministry of Agriculture created a “Yellow room” for “people who loves the yellow”.
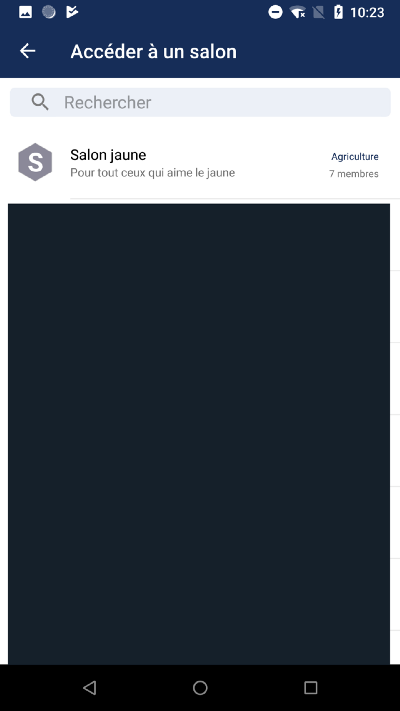


Pro-tip: Stay professional in a professional messaging app (Did I really need to say that, seriously?)
Timeline
- 9:00 am: Beginning of the analysis
- 10:15 am: Holy f***! I’m in
- 10:35 am: I gave some phone calls in order to contact the French government employee in charge of Tchap.
- 11:19 am: I disclosed the details of the vulnerability to the Matrix security team.
- 2:00 pm: Matrix fixed the issue on the Tchap backend https://twitter.com/matrixdotorg/status/1118859344790077441
- 5:42 pm: Phone call with French government officials
- 7:48 pm: Matrix published a blog post to explain the security issue in details: Security Update: Sydent 1.0.2 | Matrix.org blog
Press Coverage
- La messagerie Tchap victime d'une faille béante dès son lancement
- Tchap, la messagerie sécurisée du gouvernement victime d'une faille de sécurité
- A peine lancée, la messagerie souveraine Tchap déjà victime d'une faille béante
- La nouvelle messagerie sécurisée de l'État français déjà piratée
- "Tchap", la messagerie chiffrée du gouvernement, déjà victime d'une faille de sécurité
References
- Patch made by Matrix to fix the issue:
Update 19/04/19 11h54: I published a technical thread on Twitter to explain the vulnerability in details: thread
The parseaddr method from the Python email.utils module is RFC compliant but it’s not doing the job correctly. An issue on the Python bug tracker is opened since 2018–07–19: Issue 34155: email.utils.parseaddr mistakenly parse an email - Python tracker