MFSocket: A Chinese surveillance tool

It is well known that China spies on its fellow citizens. In this article I will tell you the story of an Android application called MFSocket, a new monitoring tool made in China. This tool allows the police to extract from the victim’s phone a lot of data such as calendar events, SMS, MMS, videos, contacts, Telegram contacts, …
The Story
On June 21, 2019 Muyi Xiao, a Chinese journalist, posted on Twitter a thread on an Android application called MFSocket. On Chinese social networks people started to report about police checking people’s phones in Beijing and Shanghai and she decided to investigate.
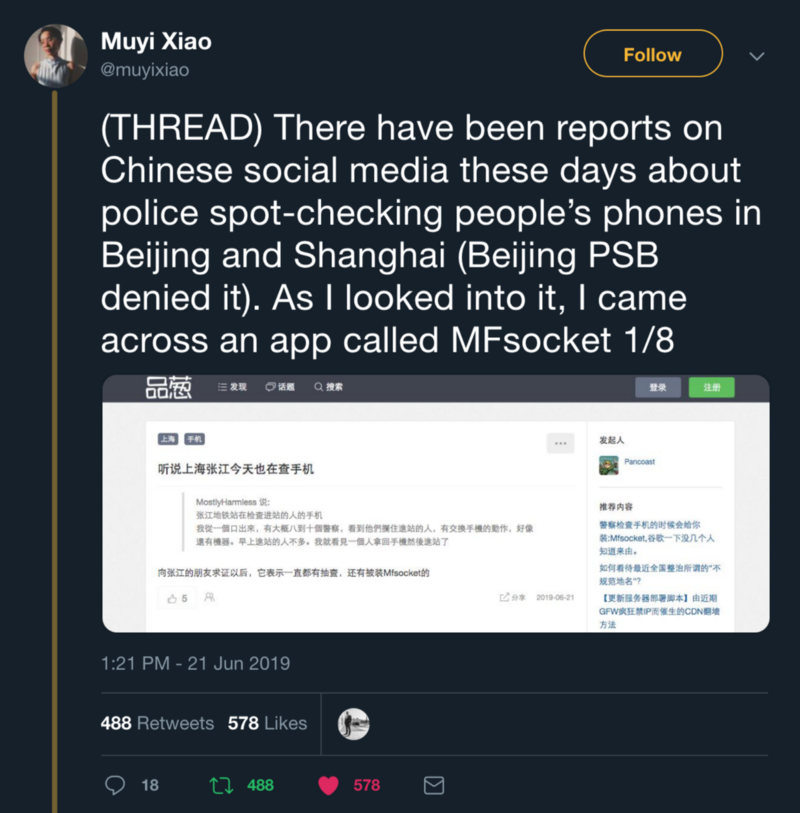
Indeed by searching ‘MFSocket’ on Google I find this type of report:
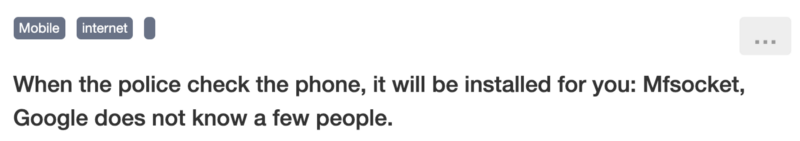
- “When the police check the phone, it will be installed for you: Mfsocket”
- “Yesterday, the company asked us to go to the police station, and then the police installed a software called MFsocket. I thought it was monitoring software!”
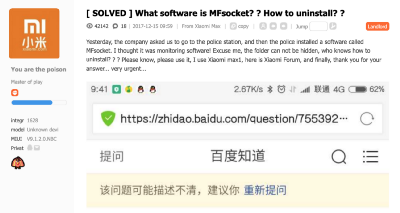
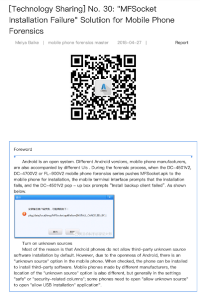
In her thread, Muyi mentioned the company behind MFSocket. She found a troubleshoot guide which link the app to a company called Meiya Pico.
Meiya Pico is not a new player. In two excellent articles, Reuters and the Wall Street Journal exposed them as a Chinese firm who sell forensics products to the Chinese authorities.

Important info from the troubleshoot guide. The police seems to use Windows to operate the app. Interesting, we will use this info later.
Muyi did a fantastic journalistic job, now it’s time to do my job. Am I able to technically confirm what she found? What are the technical capabilities of MFSocket?
Technical Analysis
Overview
The first task was to find a sample of the app. I searched “MFSocket” on Koodous and I got 48 different samples.
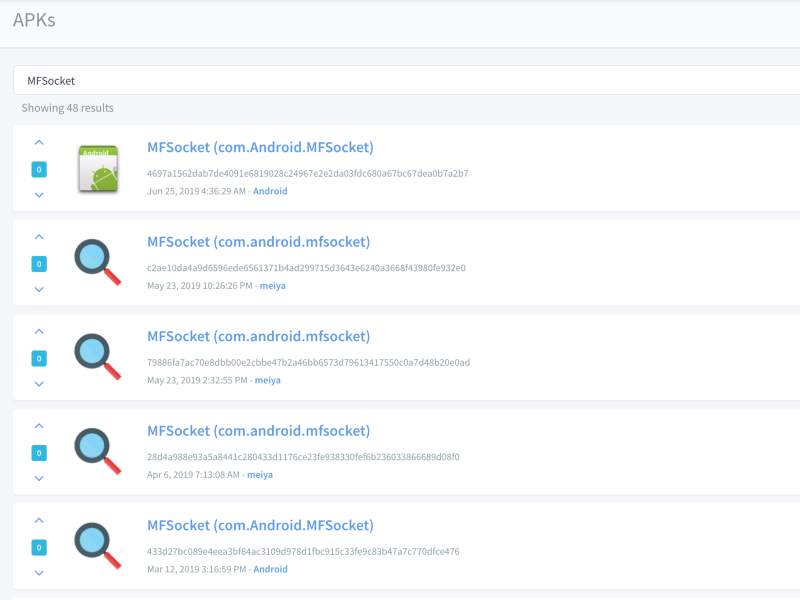
After building an Android app, the developer must sign his app with his own certificate. You can consider the certificate as the company identity card. In this case, 3 different certificates were used to sign MFSocket which is unusual.


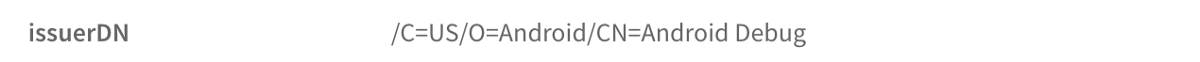
Hey, look at this! In 2 of the 3 certificates we can find the name of the Meiya Pico company. Muyi was right, we can say with a high probability that Meiya Pico is behind MFSocket. It’s time for fun and see what this app is made of!
AndroidManifest.xml
When you analyse an Android app you should always start by looking at the AndroidManifest.xml. Without looking at the code, it will give you an idea of what the app is doing. First, the permissions.
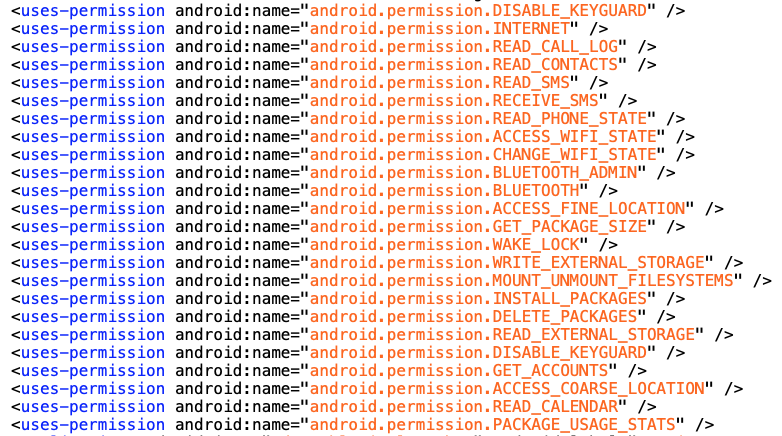
This app is asking a lot of dangerous permissions:
- Read your call log, your contacts, your SMS, your calendar, your SD card
- Disable the lock screen
- Access your location
- Install a new app without your consent
- …
Having so much dangerous permissions in the same app is a first alarm.
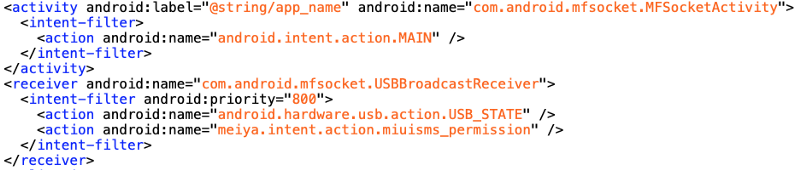
Another alarm! This app, ask a lot of dangerous permissions, but is only made of an activity and a receiver. Moreover, we can see that the activity doesn’t have the category launcher which means that this app doesn’t have an icon. So how the police is launching the app without an icon? By using the Windows software we saw above in the troubleshoot guide!
File hierarchy
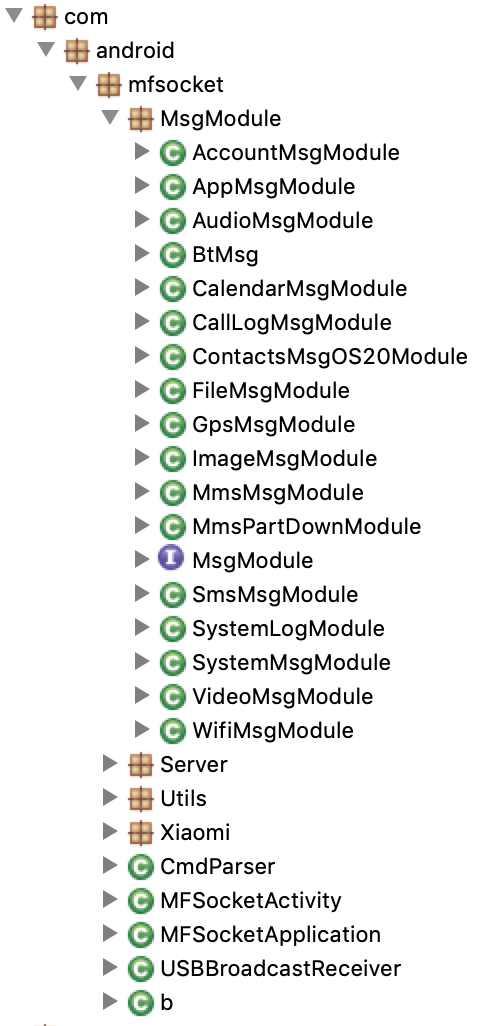
Please note that the code was obfuscated, I renamed everything to the original names.
By only looking at the image above, we already have a lot of information:
- MsgModule package: We have the confirmation that this app is a surveillance tool. The file names show that this app use all the dangerous permissions mentioned in the AndroidManifest,xml
- Server package: It’s running a server
- Xiaomi package: Something special is done/needed with Xiaomi phones
- CmdParser file: It’s able to receive and parse command
- USBBroadcastReceiver file: Something is happening when the policeman plug/unplug the victim’s phone from his computer
Communication Analysis
Did you notice? This app run a server and receive commands. In general, this is the opposite, an Android app is sending data to a server not the opposite.
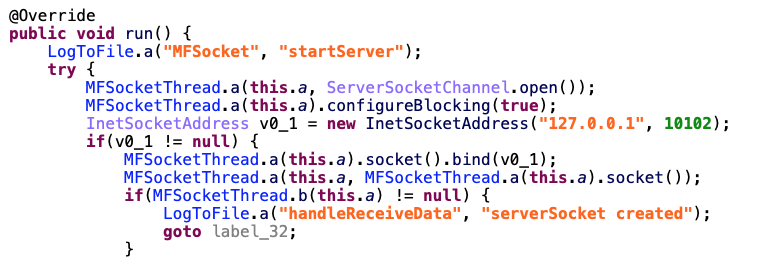
In the startServer method, MFSocket is opening locally the port 10102 of your phone and wait a command.

As expected, I launched the app and locally the port 10102 was open. We have another info, this is something local, this tool is not made to send remotely a command to the victim’s phones.
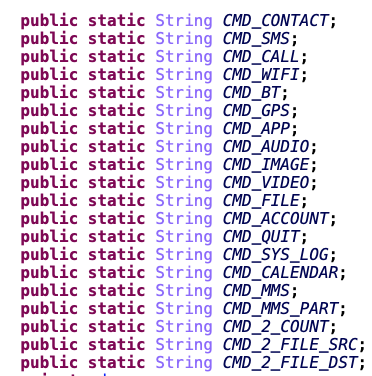
The name of the available commands are clear. With this app, the policeman is able to get contacts, sms, call log, locations, apps, audio files, image files, calendar events, …
USBBroadcastReceiver
It’s very rare to see a receiver for USB events. An end user application don’t need that in general. So why do they need it in this case?
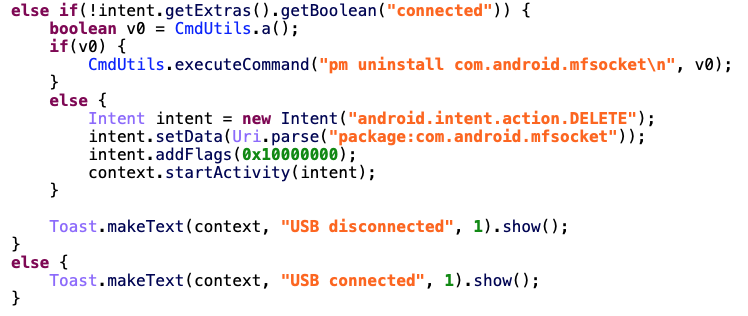
This is cristal clear, when the policeman unplug the victim’s phone from his computer, the app will uninstall itself. No trace left. This is sneaky.
MsgModule Package
I already mentioned a lot what type of data this app is able to extract. Let see some of the MsgModule.
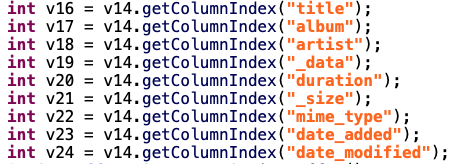
In AudioMsgModule, they will be interested by the title, album, artist, the date you added the audio file, …
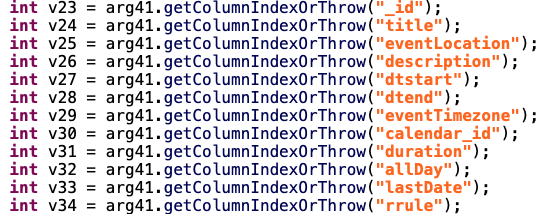
In CalendarMsgModule, they are extracting all the information contained in your calendar: title of the event, location, description, start time, end time, …
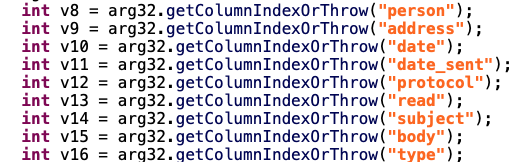
Obviously in SmsMsgModule, they take all your SMS with the meta data: person, address, date, protocol, …
In ContactsMsgOS20Module, they are after your Telegram contacts.
Final Scenario
Imagine you are a Chinese citizen, your company asked you to go the police station.
You: Hi Mr Policeman!
Policeman: Hi! May I have your phone?
You: Sure. Here it is
Policeman: Can you unlock it?
You: Sure of course
Policeman: Sit down here and wait
Meanwhile the policeman is going to his desk, plug your phone to his computer. He is using the Meiya Pico Windows software to install MFSocket. When the install is complete, with one click he is extracting all your personal data from your phone. Few minutes later, the extraction is successful. The officier unplug your phone from his computer, the app will uninstall itself.
Policeman: You can take your phone. Thank you for your collaboration.
You: Thank you sir. Have a nice day!
Policeman: You too.
Conclusion
This is sick and this is not a fictional scenario. This is the reality.
Ask yourself these questions:
- Did you notice the level of the details in the extracted data, why do they need so much data?
- After the extraction by the policeman, where do they send this data?
- Imagine this scene, in your country. Scary, right?
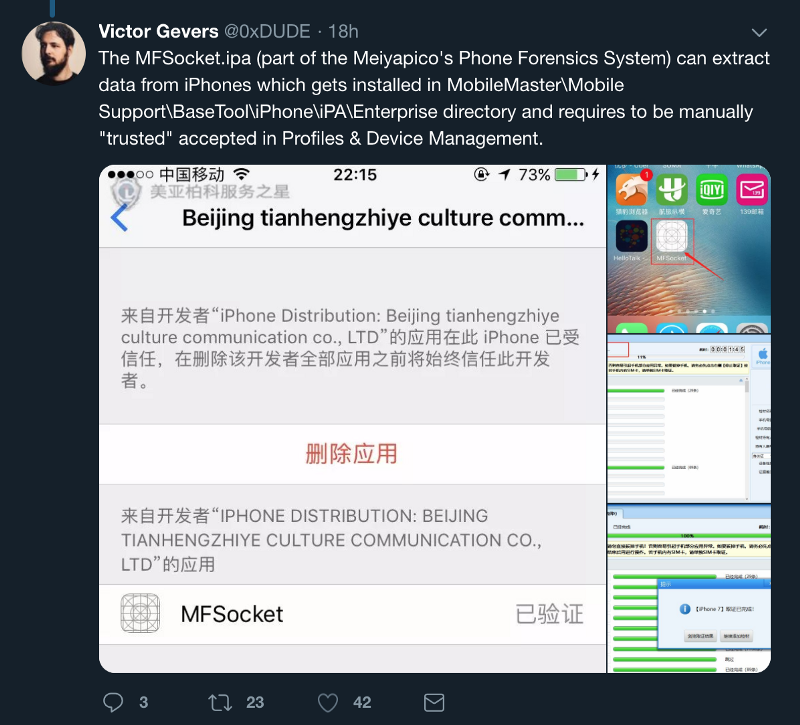
Update 26/06/19: The awesome Victor Gevers published a Twitter thread about MFSocket for iOS